- Learn with Cisco at Cisco Live 2025 in San Diego
- This Eufy robot vacuum has a built-in handheld vac - and just hit its lowest price
- I highly recommend this Lenovo laptop, and it's nearly 50% off
- Disney+ and Hulu now offer prizes, freebies, and other perks to keep you subscribed
- This new YouTube Shorts feature lets you circle to search videos more easily
Are Password Managers Safe to Use? (Benefits, Risks & Best Practices)
Yes. Password managers are a safer way to manage and secure passwords than any other approach. They may not be perfect, but what are the alternatives—posting notes on computer screens, keeping a file of passwords saved on your desktop, using the same two or three passwords over and over with variations or sticking to default passwords like “admin” or “1234”?
SEE: Keeper Password Manager Review: Features, Pros & Cons (TechRepublic)
Hackers love those who use these methods as they are easier to crack than the complex and random passwords generated by password managers. Think about all the movies where the person wanting to access a computer uses a date of birth or favorite sports teams to crack a login.
That isn’t to say that password managers don’t have frailties. Once you know the master password, you can access all associated accounts. But adherence to best practices such as adding two-factor authentication can minimize those risks.
How do password managers work?
A password manager is basically an app or vault that stores your passwords, so there is no need to remember them. The user simply logs into the password manager using a master password. Once unlocked, the password manager app uses the passwords stored in its encrypted vault to access all other user accounts. For account setups or first-time logins, the password manager generates long and complex passwords for each site or application and enters them into websites and apps automatically.
Those using password managers are advised to turn on and always use two-factor authentication. With that on, a criminal who knows the master password won’t be able to access user data and logins as they can’t provide the code or biometric input called for in 2FA. Additionally, password manager users should create a strong password as the master—one they can easily remember but is long enough and has a variation of upper and lowercase letters, symbols and numbers to thwart hackers.
Once you purchase a password manager, it needs to be downloaded onto your computer and/or mobile device. You’re walked through the stages of setting a master password, activating 2FA and choosing the best authentication method, adding password extensions to browsers and logging in to your various accounts to change existing passwords. The changed passwords are generated by the password manager, encrypted and stored in its secure vault.
For readers interested in a video version of this explainer, I highly encourage you to check out our Password Managers 101 feature available now on the official TechRepublic YouTube channel.
There, we cover the different features and advantages you get with password managers, what kind of businesses or individuals can benefit from these products and some best practices you should follow with password manager solutions.
Types of password managers
There are several different types of password manager: cloud-based (online), offline and stateless. There are gray areas between them and some vendors offer products that span two of these categories. Further ways of differentiating relate to how well suited the various solutions are to certain platforms and operating systems such as MacOS. Nevertheless, these three broad categories cover most of the ground.
Cloud-based password managers
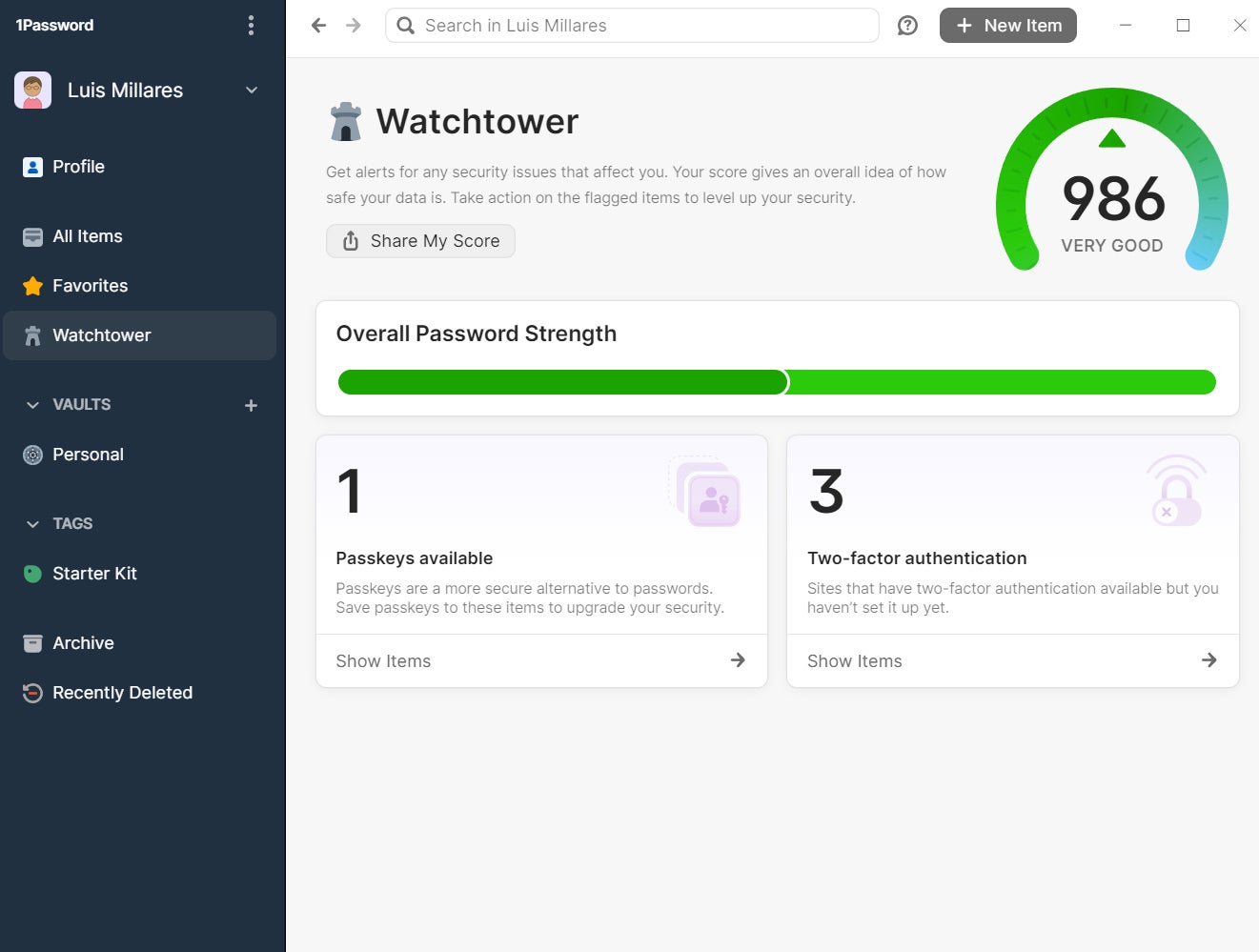
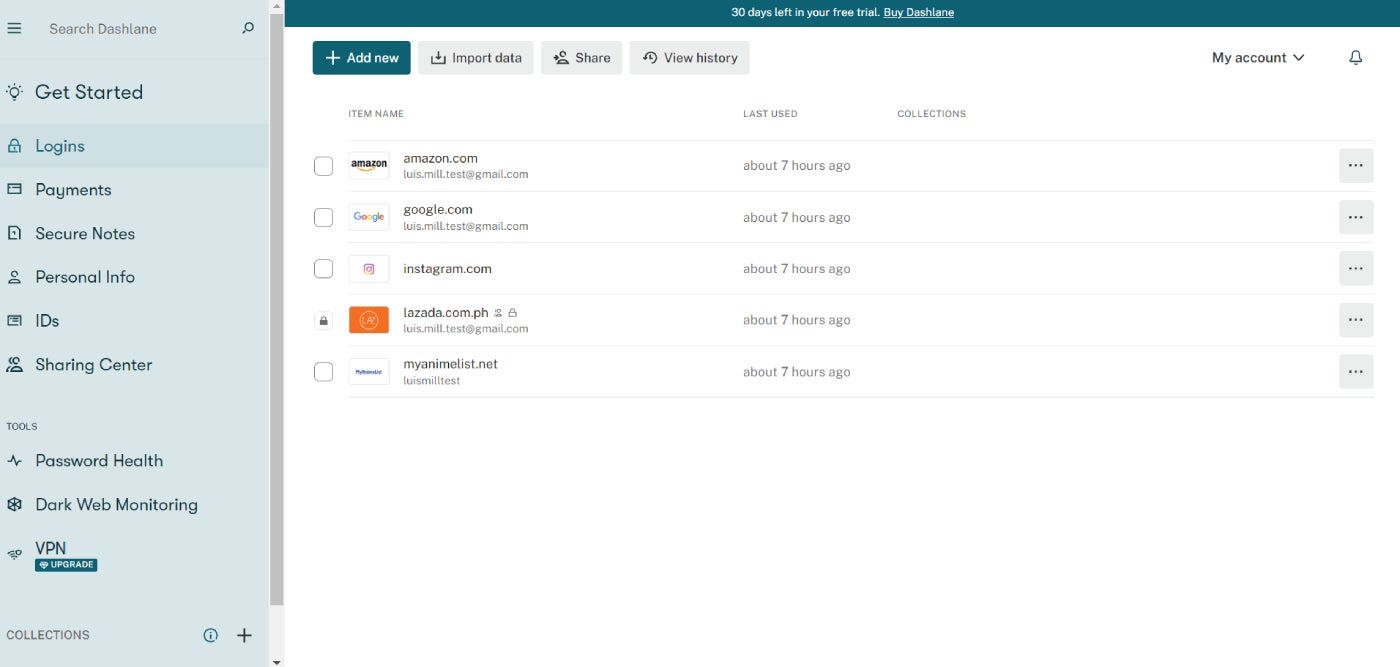
Cloud-based password managers are also known as online password managers. All passwords are stored in the cloud, typically on the provider’s server. Some free and cheap consumer password managers lack the full range of security safeguards. They may have weak or no encryption, no 2FA and their password vaults may lack enterprise-class protection features. The best ones use a zero-knowledge approach whereby user data is encrypted before the user sends it to the provider’s network.
Security duties are split between the cloud provider and the user. The provider ensures that its systems can’t be accessed by outside prying and unauthorized eyes. It provides encryption capabilities to protect that data. However, it is up to the user to prevent compromise of master passwords, to take steps to avoid being infected by a keylogger and to keep 2FA turned on and secure.
1Password, Dashlane and Keeper are password managers offering cloud-based services.
Pros
- Access your password vault from any device anywhere.
- Convenient and user-friendly.
- Built in random password generator.
- Passwords are synchronized across all devices.
Cons
- Vault is available for access attempts to third-parties.
- Keylogger malware can be used to learn your master password.
Offline password managers
Offline password management solutions store passwords directly on the user device, whether that is a smartphone, PC or laptop. They are stored locally in an encrypted vault. There is no reliance on external servers to manage and store passwords.
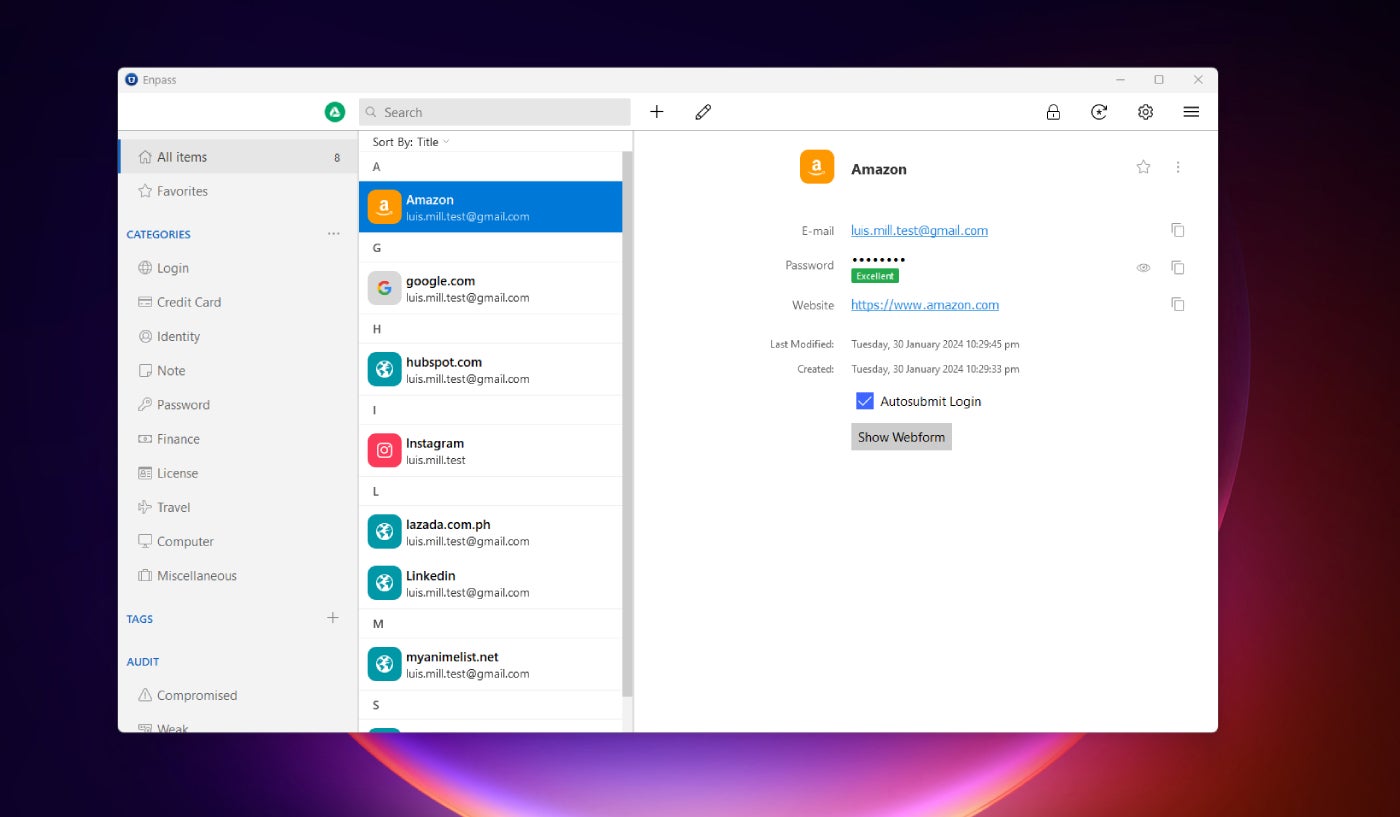
Enpass and KeePass are good examples of offline password managers. These tools offer offline password management; passwords are stored offline in a secure and encrypted vault and a master password is needed to log in.
Pros
- Lowers the risk of external actors breaching a password vault.
- Passwords are inaccessible from any other device unless synchronized with the main device.
- A higher level of control and privacy away from public networks.
- Access anytime, even without Wi-Fi.
Cons
- Requires regular back-ups.
- Doesn’t seamlessly sync between multiple mobile devices.
- If you lose the device, you lose the vault.
Stateless password managers
Stateless password managers (aka token-based) generate a unique password for each website or service rather than storing passwords directly. The generated passwords depend on a master password and an identifier or token such as a USB key, a code generated by an authenticator or a text-based code to a mobile phone. Google Titan Security Key and Dashlane use this approach. To use these stateless solutions, there’s no need for synchronization between devices as there is no database or vault to access.
Pros
- Credentials are stored in a separate device.
- No need to sync different devices.
- Hackers have no vault or known password to crack.
Cons
- If you lose your device, you lose your access.
- This method usually requires proprietary hardware and software.
Are free password managers safe?
There are many free password managers out — including KeePass, Bitwarden, RoboForm and other open-source options.
There are also browser-based password managers that are integrated tightly into a specific browser. While convenient and easy to use, it may not be easy to access passwords stored in one browser password manager from another. Also, once a hacker gains access to a device, they can access all passwords as the browser assumes that the user is authorized.
Free password managers are largely designed for the individual or family user, though some may work for small businesses. But they each suffer due to limited security features, lack of enterprise functionality and limitations on the number of users. Anyone dealing with sensitive information or operating in a business environment is advised to opt for a business-class password manager.
Safest password managers for 2024
Here are some of our top picks when it comes to the safest password managers around that work well for individuals, small teams and large enterprises.

ManageEngine Password Manager Pro includes a secure vault, robust access controls, secure remote locations and periodic password rotation.

Norton Password Manager features 256-bit AES encryption, TLS secure connections and local data encryption.

Dashlane offers a patented security architecture and AES 256-bit encryption as well as unlimited password sharing and dark web monitoring.

1Password features single sign-on, streamlined provisioning, customization of policy management and a Secrets Automation tool.

Keeper features 2FA, an encrypted vault, biometric login, as well as a single sign-on option in its advanced tier.

Bitwarden can generate, consolidate and autofill strong and secure passwords for all accounts, create and manage unique passwords and passkeys and securely share encrypted information directly.
Password management best practices
Password managers eliminate much of the risk inherent in operating online. But not all of it. Here are some best practices that can strengthen security and minimize the chances of a breach.
Use multi-factor authentication
MFA should be implemented in conjunction with password management software to ensure safety and overall security. By adding an extra step once the master password is entered, such as a biometric, authenticator or text-based code that needs to be entered, hackers will find it extremely difficult to gain access even if they know the master password.
Implement device security
Some password managers use a fob or USB stick to access passwords. Others require a master password. But the device itself should be independently secured. Ensure a password or biometric is needed to open a device and set it up to automatically lock after a few minutes of inactivity.
Keep master passwords secure
All the benefits of a password manager can be undone if the user writes down the master password on a sticky note or shares it with others. Keep your master password safe.

